
PUSH Group
Privacy & Usable Security Human-centered Computing
Our research broadly examines issues related to the usability, security and privacy for mobile device authentication. More specifically, we examine the ways in which current authentication mechanisms are used, analyze the passcodes that are selected, investigate attitudes related to security and privacy among different user groups, and investigate shoulder-surfing vulnerability in order to establish baseline measurements. Our research also examines the feasibility of technologies to resist observer and guessing attacks. Guidance developed from our studies aims to support mobile device users when authenticating, and aid interface designers when developing unlock mechanisms. The research is a collaborative effort between George Washington University and UMBC. Our research has been funded through the Office of Naval Research.






Projects
|
Impact of Grid Size for Unlock Mechanisms on Mobile Devices
|
|
|
Mobile devices on the Android OS can be unlocked by “drawing” a pattern that connects a sequence of contact points arranged in a 3x3 grid. However, patterns selected for small grids are known to be guessable. We investigated whether increasing the grid size increases the security of human-generated patterns. Our findings suggest both yes and no.
|
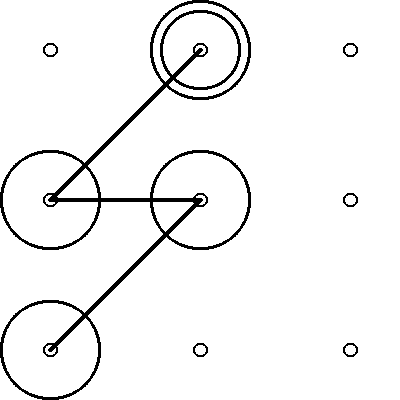 Stroke based graphical pattern
Stroke based graphical pattern
|
|
Publications: ACSAC 2015, SOUPS 2015 Poster, IEEE Internet Computing 2017
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC) Students: Devon Budzitowski (USNA), Flynn Wolf (UMBC) |
|
|
H4Plock – A gestural and tactile solution to support mobile authentication
|
|
|
H4Plock aims to support authentication and better resist observer attacks. In order to authenticate, the user enters up to four pre-selected on-screen free-form gestures, informed by tactile prompts. The system has been designed in such a way that the sequence of gestures will vary on each authentication attempt, reducing the capability of a shoulder surfer to recreate entry.
|
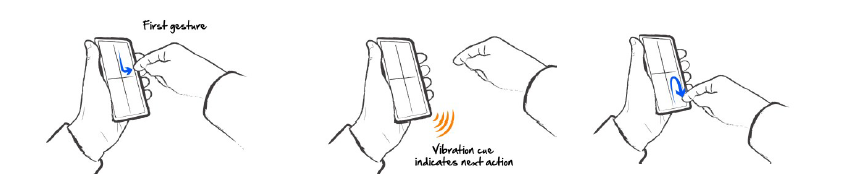 Steps to authenticate using H4Plock
Steps to authenticate using H4Plock
|
|
Publications: SOUPS 2015 Poster, iConference 2016
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC) Students: Abdullah Ali (UMBC) |
|
|
Brain Computer Interfaces for Authentication
|
|
|
Our research has examined the feasibility of Brain–Computer Interface (BCI) and gestural technologies to support the process of authentication. Unlike other input modalities, tokens detected using a BCI headset (e.g., “push,” “lift,” “excitement”), can overcome some of the security vulnerabilities associated with PIN authentication (e.g., observations from third parties). A study was conducted to compare performance against 4 digit PINs. The work was then extended to identify the benefits of these technologies for individuals who are blind.
|
 Emotiv Epoc used for study
Emotiv Epoc used for study
|
|
Publications: IJHCI 2017, ASSETS 2017
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC) Students: Charles Lechner (UMBC), Sidas Saulynas (UMBC) |
|
|
Supporting Non-Observable/Eyes-Free Authentication
|
|
|
When faced with the threat of observational attacks, mobile device users may attempt to mask the graphical interface to authenticate entry, to reduce the likelihood of third parties viewing and recreating the authentication sequence. A study was conducted examining the efficacy of authenticating entry using both PINs and graphical patterns when the mobile interface is outside of the line of sight of third parties and the user (termed: non-observable). A tactile aid to support assistive spatialization was also evaluated. A classification process has been conducted on gesture traces to identify strategies taken for unlocking and using tactile feedback.
|
 Using interface while outside line of sight
Using interface while outside line of sight
|
|
Publications: SOUPS 2016 Poster, USEC 2016, ASSETS 2017, JISA 2018, USEC WIP 2018
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC) Students: Flynn Wolf (UMBC), KC Marume (UMBC) |
|
|
Developing Baseline Measurements for Shoulder Surfing Analysis
|
|
|
A comprehensive study of shoulder surfing was conducted based on video recordings of a victim authenticating, to better understand how attacks can be affected by different factors. Authentication type and length, observation angle, phone size and method of interaction were varied. Findings which can both help inform users to improve their security choices, as well as establish baselines for researchers.
|
 Focused view shown to participants
Focused view shown to participants
|
|
Publications: ACSAC 2017, CHI 2017, ACSAC 2018
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC) Students: John Davin (USNA), Flynn Wolf (UMBC), KC Marume (UMBC) |
|
|
Understanding User Selections of Passcodes
|
|
|
Studies have been undertaken to analyze the impact of collection methods and demographics, and examine the impact of alphabet and culture on graphical passcodes.
|
|
|
Publications: SOUPS 2016 Poster, SOUPS 2016 Workshop, USEC 2016
Faculty: Adam J Aviv (USNA) Students: Justin Maguire (USNA), Jeanne Luning Prak |
|
Attitudes Towards Security and Privacy
|
|
|
Empirical investigations have been undertaken to examine the difficulties balancing security and usability for mobile interactions. Our work has specifically examined the needs of security-conscious users, whose attitudes and usage behaviors differ to those with lower levels of security training/exposure, and examined adoption of technologies such as biometrics. Our research has also examined the ways in which user attitudes towards privacy and security relating to mobile devices and the data stored thereon may impact the strength of unlock authentication, focusing on Android’s graphical unlock patterns.
|
|
Publications
Papers and Extended Abstracts
2020-2021
- Wolf, F., Aviv, A.J. & Kuber, R., 2021: Security Obstacles and Motivations for Small Businesses from a CISO's Perspective. In proceedings of 30th USENIX Security Symposium (USENIX Security 21).
- Ray, H., Aviv, A.J. & Kuber, R., 2021: Why Older Adults (Don't) Use Password Managers. In proceedings of 30th USENIX Security Symposium (USENIX Security 21).
- Ray, H., Wolf, F., Kuber, R. & Aviv, A.J., 2021: “Warn Them” or “Just Block Them”?: Using Drawmetrics to Compare Privacy Concerns Among Older and Working Age Adults.” Privacy Enhancing Technologies Symposium (2), 27-47.
- Golla, M., Rimkus, J., Aviv, A.J., & Dürmuth, M., 2019: Work in Progress: On the In-Accuracy and Influence of Android Pattern Strength Meters. In Proceedings of Workshop on Usable Security - USEC 2019, San Diego, CA.
- Ray, H. Wolf, F., Kuber, R. & Aviv. A.J., 2019: "Woe is me:" Examining Older Adults' Perceptions of Privacy. In Extended Abstracts of the Conference on Human Factors in Computing Systems - CHI’19, Glasgow, UK.
- Wolf, F., Kuber, R. & Aviv. A.J., 2019: "Pretty Close to a Must-Have:" Balancing Usability Desire and Security Concern in Biometric Adoption. In Proceedings of the Conference on Human Factors in Computing Systems - CHI’19, Glasgow, UK, Paper 151
- Aviv, A.J., Wolf, F., & Kuber, R., 2018: Replicating Video Based Shoulder Surfing for Mobile Unlock Authentication with Live Simulation. In Proceedings of 34th Annual Computer Security Applications Conference - ACSAC’18, San Juan, Puerto Rico, 453-466.
- Wolf, F., Aviv, A.J. & Kuber, R., 2018: "It’s All About The Start” Classifying Eyes-Free Mobile Authentication Techniques. Journal of Information Security and Applications, 41, 28-40. DOI: 10.1016/j.jisa.2018.05.004.
- Aviv, A.J. & Kuber, R., 2018: Towards Understanding Connections between Security/Privacy Attitudes and Unlock Authentication. In Proceedings of Workshop on Usable Security - USEC 2018, San Diego, CA.
- Wolf, F., Kuber, R. & Aviv. A.J., 2018: An Empirical Study Examining the Perceptions and Behaviours of Security-Conscious Users of Mobile Authentication. Behaviour and Information Technology, 37(4). DOI: 10.1080/0144929X.2018.1436591.
- Wolf, F., Aviv, A.J. & Kuber, R., 2018: Performance of Eyes-Free Mobile Authentication. In Proceedings of Workshop on Usable Security - USEC 2018, San Diego, CA. DOI: 10.14722/usec.2018.23013 (Detailed version of paper)
- Wolf, F., Kuber, R. & Aviv. A.J., 2018: How Do We Talk Ourselves Into These Things? Challenges with Adoption of Biometric Authentication for Expert and Non-Expert Users. In Extended Abstracts on Human Factors in Computing Systems - CHI’18, Montreal, Canada, LBW502.
2017
- Aviv, A.J., Davin, J.T., Wolf, F. & Kuber, R., 2017: Towards Baselines for Shoulder Surfing on Mobile Authentication. In Proceedings of 33rd Annual Computer Security Applications Conference - ACSAC’17, Orlando, FL, 486-498.
- Aviv, A.J., Kuber, R. & Budzitowski, D., 2017: Is Bigger Better When It Comes to Android Graphical Pattern Unlock? IEEE Internet Computing, 21 (6), 46-51. DOI: 10.1109/MIC.2017.4180833
- Davin, J., Aviv, A.J., Kuber, R. & Wolf, F., 2017: Baseline Measurements of Shoulder Surfing Analysis and Comparability for Smartphone Unlock Authentication. In Extended Abstracts on Human Factors in Computing Systems - CHI’17, Denver, CO, 2496-2503.
- Saulynas, S. & Kuber, R., 2017: Towards BCI and Gestural-Based Authentication for Individuals who are Blind. In Proceedings of the 19th International ACM Conference on Computers and Accessibility – ASSETS’17, Baltimore, MD, 403-404.
- Saulynas, S., Lechner, C. and Kuber, R. 2017: Towards the Use of Brain-Computer Interface Technologies as a Potential Alternative to PIN Authentication. International Journal of Human-Computer Interaction, 34 (5), 433-444 DOI: 10.1080/10447318.2017.1357905.
- Wolf, F., Kuber, R. & Aviv, A.J., 2017: Perceptions of Mobile Device Authentication Mechanisms by Individuals who are Blind. In Proceedings of the 19th International ACM Conference on Computers and Accessibility – ASSETS’17, Baltimore, MD, 385-386.
2015 - 2016
- Ali, A., Kuber, R. & Aviv, A.J., 2016: Developing and Evaluating a Gestural and Tactile Mobile Interface to Support User Authentication. In Proceedings of iConference 2016, Philadelphia, PA.
- Aviv, A.J., Budzitowski, D. & Kuber, R., 2015: Is Bigger Better? Comparing User-Generated Passwords on 3x3 vs. 4x4 Grid Sizes for Android's Pattern Unlock. In Proceedings of 31st Annual Computer Security Applications Conference - ACSAC’15, Los Angeles, CA, 301-310.
- Aviv, A.J., Maguire, J. & Luning Prak, J., 2016: Analyzing the Impact of Collection Methods and Demographics for Android's Pattern Unlock. In Proceedings of USEC Workshop, San Diego, CA.
- Aviv, A.J., Duermith, M., and Gupta, P., 2016: Position Paper: Measuring the Impact of Alphabet and Culture on Graphical Passwords. In the proceedings of the Who Are You?! In Proceedings of Adventures in Authentication Workshop, Twelfth Symposium on Usable Privacy and Security – SOUPS’16, Denver, CO.
- Wolf, F., Kuber, R., and Aviv, A.J., 2016: Preliminary Findings from an Exploratory Qualitative Study of Security-Conscious Users of Mobile Authentication. In Proceedings of the Second Workshop on Security Information Workers, Twelfth Symposium on Usable Privacy and Security – SOUPS’16, Denver, CO.
Posters
- Wolf, F., Kuber, R. & Aviv. A.J., 2018: How Do We Talk Ourselves Into These Things? Challenges with Adoption of Biometric Authentication for Expert and Non-Expert Users. To appear in Thirteenth Symposium on Usable Privacy and Security – SOUPS’18, Baltimore, MD. (Poster refers to pre-published CHI extended abstract)
- Wolf, F., Kuber, R. & Aviv, A.J., 2017: Addressing Observational Attacks through the Design of a Tactile Aid for Mobile User Authentication. In 33rd Annual Computer Security Applications Conference - ACSAC’17, Orlando, FL.
- Wolf, F., Kuber, R., and Aviv, A.J., 2016: Towards Non-Observable Authentication for Mobile Devices. In Twelfth Symposium on Usable Privacy and Security – SOUPS’16, Denver, CO.
- Heidt, S. and Aviv, A.J., 2016: Refining Graphical Password Strength Meters. In Twelfth Symposium on Usable Privacy and Security – SOUPS’16, Denver, CO.
- Ali, A., Kuber, R. & Aviv, A.J., 2015: H4Plock: Supporting Mobile User Authentication through Gestural Input and Tactile Output. In Eleventh Symposium on Usable Privacy and Security - SOUPS’15, Ottawa, Canada.
- Budzitowski, D., Aviv, A.J. & Kuber, R., 2015: Do Bigger Grids Sizes Mean Better Passwords? 3x3 vs. 4x4 Grid Sizes for Android Unlock Patterns. In Eleventh Symposium on Usable Privacy and Security - SOUPS’15, Ottawa, Canada.
Videos
Project: Supporting Non-Observable/Eyes-Free Authentication
Classification of on-screen gestures in non-observable conditions
Impact of tactile cues on non-observable authentication
Classification of on-screen gestures in non-observable conditions
Related Publications: SOUPS 2016 Poster, ASSETS 2017, USEC 2018
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC)
Students: Flynn Wolf (UMBC), KC Marume (UMBC)
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC)
Students: Flynn Wolf (UMBC), KC Marume (UMBC)
Project: Attitudes Towards Security and Privacy
Adoption of biometrics
Related Publications: SOUPS 2016 Workshop, BIT 2018, CHI 2018, USEC 2018, CHI 2019a
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC)
Students: Flynn Wolf (UMBC)
Faculty: Adam J Aviv (USNA), Ravi Kuber (UMBC)
Students: Flynn Wolf (UMBC)
People

Dr. Adam J. Aviv
Associate Professor George Washington University E: aaviv@gwu.edu W: https://www.adamaviv.com |
Research interests are primarily in the area of computer and network security/cybersecurity, privacy, usable security of smartphone and tablets, and mobile authentication.
|

|
Areas of interest include HCI and accessibility. More specifically, examining ways to support authentication when the visual channel is blocked, restricted or overloaded.
|

|
Research interests include examining challenges associated with authentication, designing for eyes-free interactions and for heightening situational awareness.
|

|
Research interests include examining perceptions of privacy and security among different user groups.
|
ALUMNI
UNDERGRADUATE
|
GRADUATE
|
ONR High School SEAP Interns
|
Popular Press

|
5 Incredibly Stupid Security Mistakes You Make Every Day
Published by: Gizmodo |

|
For the Love of All That Is Holy, Stop Using Pattern Unlock
Published by: Gizmodo |

|
Don't Rely On An Unlock Pattern To Secure Your Android Phone
Published by: Wired |
Contact Us
For further inquiries or for students interested in conducting independent studies/theses in areas related to usable security, please contact aaviv@gwu.edu or rkuber@umbc.edu.If funded positions are available for applicants, these will be advertised here.